26
фев
How to configure SSL VPN for Mac OS X; Feedback and contact; Applies to the following Sophos products and versions Sophos Firewall. Prerequisites This article requires that you have already set up an SSL VPN Remote Access tunnel on your Sophos Firewall. How to configure SSL VPN for Mac OS X. ShrewSoft VPN Client is not available for Mac but there are plenty of alternatives that runs on macOS with similar functionality. The most popular Mac alternative is WireGuard, which is both free and Open Source. If that doesn't suit you, our users have ranked 21 alternatives to ShrewSoft VPN Client and 14 are available for Mac so hopefully you can find a suitable replacement.
Objective
There is no Quick VPN version suitable for Mac OS. However, there is an increasing number of users who would like to deploy a Quick VPN alternative for Mac OS. In this article, IP Securitas is used as an alternative for a Quick VPN.
Note: You need to download and install the IP Securitas on your MAC OS before you start configuration. You can download it from the following link:
This article explains how to deploy a Quick VPN alternative for Mac OS on Rv016, RV042, RV042G and RV082 VPN Routers.
Applicable Devices
• RV016
• RV042
• RV042G
• RV082
Software Version
• v4.2.2.08
Deploy a Quick VPN Alternative for Mac OS
Note: The VPN Client to Gateway configuration of the device needs to be done first. To know more how to configure VPN Client to Gateway refer to Set Up a Remote Access Tunnel (Client to Gateway) for VPN Clients on RV016, RV042, RV042G and RV082 VPN Routers.
Step 1. Run the IP Securitas on the Mac OS. The IPSecuritas window appears:
Step 2. Click Start.
Step 3. From the menu bar, choose Connections > Edit Connections. The Connections window appears.
Step 4. Click the + icon to add a new connection.
Step 5. Enter a name for the new connection under connections.
General
Step 1. Click the General tab.
Step 2. Enter the IP address of the remote router in the Remote IPSec Device field.
Note: You do not need to configure Local Side as this configuration is for remote client. You just need to configure Remote Mode.
Step 3. In the Remote Side area, choose Network from the Endpoint Mode drop-down list.
Step 4. Enter the subnet mask in the Network Mask (CIDR) field.
Step 5. Enter the remote network address in the Network Address field.
Phase 1
Phase 1 is the simplex, logical security association (SA) between the two ends of the tunnel to support secure authenticated communication.
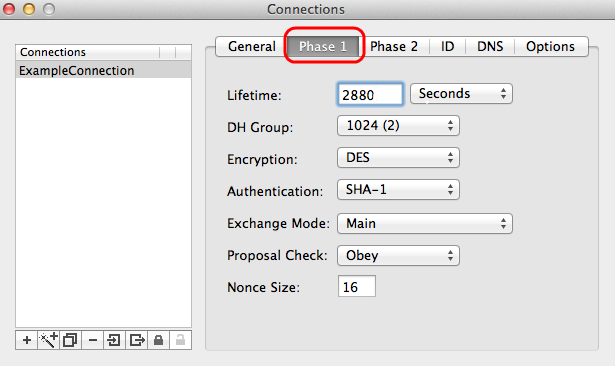
Step 1. Click the Phase 1 tab.
Step 2. Enter the lifetime you entered during the configuration of the tunnel in the Lifetime field. If time expires, a new key is renegotiated automatically. The key lifetime can range from 1081 to 86400 seconds. The default value for Phase 1 is 28800 seconds.
Step 3. Choose the appropriate time unit for the Lifetime from the Lifetime drop-down list. The default is seconds.

Step 4. Choose the same DH Group which you entered for the configuration of the tunnel from the DH Group drop-down list. The Diffie-Hellman (DH) group is used for key exchange.
Top 4 alternatives to minipad2 for mac. Step 5. Choose the encryption type from the Encryption drop-down list which you entered for the configuration of the tunnel. The Encryption method determines the length of the key used to encrypt/decrypt Encapsulating Security Payload (ESP) packets.
Step 6. Choose the authentication method which you entered for the configuration of the tunnel from the Authentication drop-down list. The type of authentication determines the method to authenticate ESP packets.
Step 7. Choose the appropriate exchange mode from the Exchange Mode drop-down list.
• Main — Represents exchange mode for all type of gateway except Full Qualified Domain Name (FQDN).
• Aggressive — Represents the exchange mode for Full Qualified Domain Name (FQDN) gateway.
Phase 2
Phase 2 is the security association to determine the security of the data packet during the data packets pass through the two end points.
Step 1. Click the Phase 2 tab.
Step 2. Enter the same lifetime in the Lifetime field which you entered for the the configuration of the tunnel and also Phase 1.
Step 3. Choose the same time unit of the lifetime from the Lifetime drop-down list which you entered for the configuration of the tunnel and Phase 1.
Step 4. Choose the same DH group from the Perfect Forwarding Secrecy (PFS) Group drop-down list which you entered for the the configuration of the tunnel.
Step 5. Uncheck all the unused Encryption and Authentication methods. Only check the ones defined under the Phase 1 tab.
ID
Step 1. Click ID tab.
Step 2. Choose the same method of local identifier as the tunnel from the Local Identifier drop-down list. Enter the appropriate value according to the type of local identifier if needed.
Step 3. Choose the same method of remote identifier as the tunnel from the Remote Identifier drop-down list. Enter the appropriate value according to the type of remote identifier if needed.
Step 4. Choose the same authentication method as the tunnel from the Authentication Method drop-down list. Enter the appropriate authentication value according to the type of authentication method if needed.
Step 5. Click the x icon (red circle) to close the connection window. This automatically saves the settings. The IPSecuritas window appears.
Connection
Step 1. In the IPSecuritas window, click Start. The user is then connected to access the VPN.
Back to My Mac is a subset of iCloud that allows a user to remotely access any Mac on the same iCloud account. Whether you need to access files or control the desktop directly, Back to My Mac made it easy for an iCloud account user to get connected from anywhere.
Unfortunately, Apple pulled the plug on the Back to My Mac iCloud feature in all versions of macOS as of July 1. Here are some alternatives to maintain connectivity to your remote Macs!
Accessing files
If you are up-to-date with the latest macOS and iOS revisions then you're likely already familiar with sharing files via iCloud Drive. iCloud Drive already allows you to edit and sync files automagically on Apple centric hardware but you can even get access from other platforms on iCloud.com. iCloud Drive offers 5 GB of storage for free with more storage available for a fee. To enable iCloud Drive, do the following.
- Start System Preferences.
- Select iCloud.
- Check iCloud Drive.
Accessing your desktop
Apple offers two already built-in tools to enable desktop access 'remotely'. I'm placing the word remotely in quotes since this means that you Mac will have the ability to accept remote connections but will only be accessible from computers on the same network unless further somewhat complicated (and potentially insecure) configurations are made.
Eclipselink jdbc drivers for mac. Database Support. EclipseLink supports any relational database that is compliant with SQL and has a compliant JDBC driver. EclipseLink has extended support for several database platforms. The extended support mainly consists of providing native sequencing support, schema creation, and certain database functions. The databases in Table A-1 are.
One issue is that of dynamically assigned IP addresses provided by your ISP. If you do not have a statically assigned IP (which you can have depending on your ISP), you'll need a paid service such as Dyn DNS services to translate dynamic IPs to static names so that your remote computer can be found on the internet for you to connect to.
Another issue is ensuring that the connections to your remote Mac can pass through firewalls and be properly routed to an internal network from the Internet.
If you already have a method for connecting to your home/work network remotely such as via a VPN or through an ssh tunnel, then these built-in Apple provided methods will work just fine for you.
Screen Sharing
Screen sharing is exactly what it sounds like. You'll be sharing the screen of a Mac and as such any thing you do on that screen will be visible to both the local and remote user. You can initiate a connection via finder from under the shared sidebar or via a VNC client such as TightVNC.
To enable Screen Sharing do the following.
- Start System Preferences.
- Select Sharing.
- Check Screen Sharing to on.
Apple Remote Desktop
Apple Remote Desktop is the bigger more capable brother to Screen Sharing. Of the plethora of things ARD can do such as manage multiple computers, take inventory, and deploy software, it too has a remote screen sharing capability. It's a bit of overkill for simple screen sharing and data access but you can get more information from Apple directly if you think you're the type to take advantage of all of the features. Like Screen Sharing, you'll need to roll your own out of network connection method, like VPN or the like, and you can use both the Finder and a VNC client to make a remote screen connection. Here's how to setup Apple Remote Desktop on your Mac.
- Start System Preferences.
- Select Sharing.
- Check Remote Management to on.
Third party solutions
If you're not the type to want to configure VPNs or firewalls to enable internet screen and file sharing access, you'll be happy to know that there do exist third party programs you can purchase that allow for Back to My Mac capabilities.
Screens 4
Edovia Screens 4 allows for Desktop access (For around $30) with an optional remote internet access service called Screens Connect that takes care of all of the dirty connectivity work for you. It's easy to setup and syncs across all of your iCloud devices with both macOS and iOS versions. It is completely compatible with VNC server/client software.
LogMeIn
LogMeIn offers a robust Remote Desktop solution that isn't VNC compatible but has its own proprietary Remote Desktop client software that takes care of all of the connectivity issues. Although costly at around $350/year, it's used by professional individuals and businesses alike and offers excellent support services for those times that access to your Mac's Remote Desktop is critical.
Final comments
I'm the type of person that likes to roll my own Remote Desktop solutions by using FOSS wherever possible. I'm lucky enough to have a static IP at my home so connectivity is not an issue when I am traveling. I use it nearly every time I travel. Will losing Back to My Mac be an issue for you? Will you roll out your own solution or will you have to pay for a third party for remote connections to your desktop and files? Do you have other suggestions for Remote Desktop access? Let us know your thoughts in the comments!
Related resources
We test and review VPN services in the context of legal recreational uses. For example:
1. Accessing a service from another country (subject to the terms and conditions of that service).
2. Protecting your online security and strengthening your online privacy when abroad.
We do not support or condone the illegal or malicious use of VPN services. Consuming pirated content that is paid-for is neither endorsed nor approved by Future Publishing.
We may earn a commission for purchases using our links. Learn more.
U.S. and Afghan forces successfully captured insurgents using an iPhone app
When their specialist kit failed, soldiers turned to an iPhone to get the job done.
Objective

This article explains how to deploy a Quick VPN alternative for Mac OS on Rv016, RV042, RV042G and RV082 VPN Routers.
Applicable Devices
• RV016
• RV042
• RV042G
• RV082
Software Version
• v4.2.2.08
Deploy a Quick VPN Alternative for Mac OS
Note: The VPN Client to Gateway configuration of the device needs to be done first. To know more how to configure VPN Client to Gateway refer to Set Up a Remote Access Tunnel (Client to Gateway) for VPN Clients on RV016, RV042, RV042G and RV082 VPN Routers.
Step 1. Run the IP Securitas on the Mac OS. The IPSecuritas window appears:
Step 2. Click Start.
Step 3. From the menu bar, choose Connections > Edit Connections. The Connections window appears.
Step 4. Click the + icon to add a new connection.
Step 5. Enter a name for the new connection under connections.
General
Step 1. Click the General tab.
Step 2. Enter the IP address of the remote router in the Remote IPSec Device field.
Note: You do not need to configure Local Side as this configuration is for remote client. You just need to configure Remote Mode.
Step 3. In the Remote Side area, choose Network from the Endpoint Mode drop-down list.
Step 4. Enter the subnet mask in the Network Mask (CIDR) field.
Step 5. Enter the remote network address in the Network Address field.
Phase 1
Phase 1 is the simplex, logical security association (SA) between the two ends of the tunnel to support secure authenticated communication.
Step 1. Click the Phase 1 tab.
Step 2. Enter the lifetime you entered during the configuration of the tunnel in the Lifetime field. If time expires, a new key is renegotiated automatically. The key lifetime can range from 1081 to 86400 seconds. The default value for Phase 1 is 28800 seconds.
Step 3. Choose the appropriate time unit for the Lifetime from the Lifetime drop-down list. The default is seconds.

Step 4. Choose the same DH Group which you entered for the configuration of the tunnel from the DH Group drop-down list. The Diffie-Hellman (DH) group is used for key exchange.
Top 4 alternatives to minipad2 for mac. Step 5. Choose the encryption type from the Encryption drop-down list which you entered for the configuration of the tunnel. The Encryption method determines the length of the key used to encrypt/decrypt Encapsulating Security Payload (ESP) packets.
Step 6. Choose the authentication method which you entered for the configuration of the tunnel from the Authentication drop-down list. The type of authentication determines the method to authenticate ESP packets.
Step 7. Choose the appropriate exchange mode from the Exchange Mode drop-down list.
• Main — Represents exchange mode for all type of gateway except Full Qualified Domain Name (FQDN).
• Aggressive — Represents the exchange mode for Full Qualified Domain Name (FQDN) gateway.
Phase 2
Phase 2 is the security association to determine the security of the data packet during the data packets pass through the two end points.
Step 1. Click the Phase 2 tab.
Step 2. Enter the same lifetime in the Lifetime field which you entered for the the configuration of the tunnel and also Phase 1.
Step 3. Choose the same time unit of the lifetime from the Lifetime drop-down list which you entered for the configuration of the tunnel and Phase 1.
Step 4. Choose the same DH group from the Perfect Forwarding Secrecy (PFS) Group drop-down list which you entered for the the configuration of the tunnel.
Step 5. Uncheck all the unused Encryption and Authentication methods. Only check the ones defined under the Phase 1 tab.
ID
Step 1. Click ID tab.
Step 2. Choose the same method of local identifier as the tunnel from the Local Identifier drop-down list. Enter the appropriate value according to the type of local identifier if needed.
Step 3. Choose the same method of remote identifier as the tunnel from the Remote Identifier drop-down list. Enter the appropriate value according to the type of remote identifier if needed.
Step 4. Choose the same authentication method as the tunnel from the Authentication Method drop-down list. Enter the appropriate authentication value according to the type of authentication method if needed.
Step 5. Click the x icon (red circle) to close the connection window. This automatically saves the settings. The IPSecuritas window appears.
Connection
Step 1. In the IPSecuritas window, click Start. The user is then connected to access the VPN.
Back to My Mac is a subset of iCloud that allows a user to remotely access any Mac on the same iCloud account. Whether you need to access files or control the desktop directly, Back to My Mac made it easy for an iCloud account user to get connected from anywhere.
Unfortunately, Apple pulled the plug on the Back to My Mac iCloud feature in all versions of macOS as of July 1. Here are some alternatives to maintain connectivity to your remote Macs!
Accessing files
If you are up-to-date with the latest macOS and iOS revisions then you're likely already familiar with sharing files via iCloud Drive. iCloud Drive already allows you to edit and sync files automagically on Apple centric hardware but you can even get access from other platforms on iCloud.com. iCloud Drive offers 5 GB of storage for free with more storage available for a fee. To enable iCloud Drive, do the following.
- Start System Preferences.
- Select iCloud.
- Check iCloud Drive.
Accessing your desktop
Apple offers two already built-in tools to enable desktop access 'remotely'. I'm placing the word remotely in quotes since this means that you Mac will have the ability to accept remote connections but will only be accessible from computers on the same network unless further somewhat complicated (and potentially insecure) configurations are made.
Eclipselink jdbc drivers for mac. Database Support. EclipseLink supports any relational database that is compliant with SQL and has a compliant JDBC driver. EclipseLink has extended support for several database platforms. The extended support mainly consists of providing native sequencing support, schema creation, and certain database functions. The databases in Table A-1 are.
One issue is that of dynamically assigned IP addresses provided by your ISP. If you do not have a statically assigned IP (which you can have depending on your ISP), you'll need a paid service such as Dyn DNS services to translate dynamic IPs to static names so that your remote computer can be found on the internet for you to connect to.
Another issue is ensuring that the connections to your remote Mac can pass through firewalls and be properly routed to an internal network from the Internet.
If you already have a method for connecting to your home/work network remotely such as via a VPN or through an ssh tunnel, then these built-in Apple provided methods will work just fine for you.
Screen Sharing
Screen sharing is exactly what it sounds like. You'll be sharing the screen of a Mac and as such any thing you do on that screen will be visible to both the local and remote user. You can initiate a connection via finder from under the shared sidebar or via a VNC client such as TightVNC.
To enable Screen Sharing do the following.
- Start System Preferences.
- Select Sharing.
- Check Screen Sharing to on.
Apple Remote Desktop
Apple Remote Desktop is the bigger more capable brother to Screen Sharing. Of the plethora of things ARD can do such as manage multiple computers, take inventory, and deploy software, it too has a remote screen sharing capability. It's a bit of overkill for simple screen sharing and data access but you can get more information from Apple directly if you think you're the type to take advantage of all of the features. Like Screen Sharing, you'll need to roll your own out of network connection method, like VPN or the like, and you can use both the Finder and a VNC client to make a remote screen connection. Here's how to setup Apple Remote Desktop on your Mac.
- Start System Preferences.
- Select Sharing.
- Check Remote Management to on.
Third party solutions
If you're not the type to want to configure VPNs or firewalls to enable internet screen and file sharing access, you'll be happy to know that there do exist third party programs you can purchase that allow for Back to My Mac capabilities.
Screens 4
Edovia Screens 4 allows for Desktop access (For around $30) with an optional remote internet access service called Screens Connect that takes care of all of the dirty connectivity work for you. It's easy to setup and syncs across all of your iCloud devices with both macOS and iOS versions. It is completely compatible with VNC server/client software.
LogMeIn
LogMeIn offers a robust Remote Desktop solution that isn't VNC compatible but has its own proprietary Remote Desktop client software that takes care of all of the connectivity issues. Although costly at around $350/year, it's used by professional individuals and businesses alike and offers excellent support services for those times that access to your Mac's Remote Desktop is critical.
Final comments
I'm the type of person that likes to roll my own Remote Desktop solutions by using FOSS wherever possible. I'm lucky enough to have a static IP at my home so connectivity is not an issue when I am traveling. I use it nearly every time I travel. Will losing Back to My Mac be an issue for you? Will you roll out your own solution or will you have to pay for a third party for remote connections to your desktop and files? Do you have other suggestions for Remote Desktop access? Let us know your thoughts in the comments!
Related resources
We test and review VPN services in the context of legal recreational uses. For example:
1. Accessing a service from another country (subject to the terms and conditions of that service).
2. Protecting your online security and strengthening your online privacy when abroad.
We do not support or condone the illegal or malicious use of VPN services. Consuming pirated content that is paid-for is neither endorsed nor approved by Future Publishing.
We may earn a commission for purchases using our links. Learn more.
U.S. and Afghan forces successfully captured insurgents using an iPhone app
When their specialist kit failed, soldiers turned to an iPhone to get the job done.
...">Deploy A Quick Vpn Alternative For Mac(26.02.2020)Objective

This article explains how to deploy a Quick VPN alternative for Mac OS on Rv016, RV042, RV042G and RV082 VPN Routers.
Applicable Devices
• RV016
• RV042
• RV042G
• RV082
Software Version
• v4.2.2.08
Deploy a Quick VPN Alternative for Mac OS
Note: The VPN Client to Gateway configuration of the device needs to be done first. To know more how to configure VPN Client to Gateway refer to Set Up a Remote Access Tunnel (Client to Gateway) for VPN Clients on RV016, RV042, RV042G and RV082 VPN Routers.
Step 1. Run the IP Securitas on the Mac OS. The IPSecuritas window appears:
Step 2. Click Start.
Step 3. From the menu bar, choose Connections > Edit Connections. The Connections window appears.
Step 4. Click the + icon to add a new connection.
Step 5. Enter a name for the new connection under connections.
General
Step 1. Click the General tab.
Step 2. Enter the IP address of the remote router in the Remote IPSec Device field.
Note: You do not need to configure Local Side as this configuration is for remote client. You just need to configure Remote Mode.
Step 3. In the Remote Side area, choose Network from the Endpoint Mode drop-down list.
Step 4. Enter the subnet mask in the Network Mask (CIDR) field.
Step 5. Enter the remote network address in the Network Address field.
Phase 1
Phase 1 is the simplex, logical security association (SA) between the two ends of the tunnel to support secure authenticated communication.
Step 1. Click the Phase 1 tab.
Step 2. Enter the lifetime you entered during the configuration of the tunnel in the Lifetime field. If time expires, a new key is renegotiated automatically. The key lifetime can range from 1081 to 86400 seconds. The default value for Phase 1 is 28800 seconds.
Step 3. Choose the appropriate time unit for the Lifetime from the Lifetime drop-down list. The default is seconds.

Step 4. Choose the same DH Group which you entered for the configuration of the tunnel from the DH Group drop-down list. The Diffie-Hellman (DH) group is used for key exchange.
Top 4 alternatives to minipad2 for mac. Step 5. Choose the encryption type from the Encryption drop-down list which you entered for the configuration of the tunnel. The Encryption method determines the length of the key used to encrypt/decrypt Encapsulating Security Payload (ESP) packets.
Step 6. Choose the authentication method which you entered for the configuration of the tunnel from the Authentication drop-down list. The type of authentication determines the method to authenticate ESP packets.
Step 7. Choose the appropriate exchange mode from the Exchange Mode drop-down list.
• Main — Represents exchange mode for all type of gateway except Full Qualified Domain Name (FQDN).
• Aggressive — Represents the exchange mode for Full Qualified Domain Name (FQDN) gateway.
Phase 2
Phase 2 is the security association to determine the security of the data packet during the data packets pass through the two end points.
Step 1. Click the Phase 2 tab.
Step 2. Enter the same lifetime in the Lifetime field which you entered for the the configuration of the tunnel and also Phase 1.
Step 3. Choose the same time unit of the lifetime from the Lifetime drop-down list which you entered for the configuration of the tunnel and Phase 1.
Step 4. Choose the same DH group from the Perfect Forwarding Secrecy (PFS) Group drop-down list which you entered for the the configuration of the tunnel.
Step 5. Uncheck all the unused Encryption and Authentication methods. Only check the ones defined under the Phase 1 tab.
ID
Step 1. Click ID tab.
Step 2. Choose the same method of local identifier as the tunnel from the Local Identifier drop-down list. Enter the appropriate value according to the type of local identifier if needed.
Step 3. Choose the same method of remote identifier as the tunnel from the Remote Identifier drop-down list. Enter the appropriate value according to the type of remote identifier if needed.
Step 4. Choose the same authentication method as the tunnel from the Authentication Method drop-down list. Enter the appropriate authentication value according to the type of authentication method if needed.
Step 5. Click the x icon (red circle) to close the connection window. This automatically saves the settings. The IPSecuritas window appears.
Connection
Step 1. In the IPSecuritas window, click Start. The user is then connected to access the VPN.
Back to My Mac is a subset of iCloud that allows a user to remotely access any Mac on the same iCloud account. Whether you need to access files or control the desktop directly, Back to My Mac made it easy for an iCloud account user to get connected from anywhere.
Unfortunately, Apple pulled the plug on the Back to My Mac iCloud feature in all versions of macOS as of July 1. Here are some alternatives to maintain connectivity to your remote Macs!
Accessing files
If you are up-to-date with the latest macOS and iOS revisions then you're likely already familiar with sharing files via iCloud Drive. iCloud Drive already allows you to edit and sync files automagically on Apple centric hardware but you can even get access from other platforms on iCloud.com. iCloud Drive offers 5 GB of storage for free with more storage available for a fee. To enable iCloud Drive, do the following.
- Start System Preferences.
- Select iCloud.
- Check iCloud Drive.
Accessing your desktop
Apple offers two already built-in tools to enable desktop access 'remotely'. I'm placing the word remotely in quotes since this means that you Mac will have the ability to accept remote connections but will only be accessible from computers on the same network unless further somewhat complicated (and potentially insecure) configurations are made.
Eclipselink jdbc drivers for mac. Database Support. EclipseLink supports any relational database that is compliant with SQL and has a compliant JDBC driver. EclipseLink has extended support for several database platforms. The extended support mainly consists of providing native sequencing support, schema creation, and certain database functions. The databases in Table A-1 are.
One issue is that of dynamically assigned IP addresses provided by your ISP. If you do not have a statically assigned IP (which you can have depending on your ISP), you'll need a paid service such as Dyn DNS services to translate dynamic IPs to static names so that your remote computer can be found on the internet for you to connect to.
Another issue is ensuring that the connections to your remote Mac can pass through firewalls and be properly routed to an internal network from the Internet.
If you already have a method for connecting to your home/work network remotely such as via a VPN or through an ssh tunnel, then these built-in Apple provided methods will work just fine for you.
Screen Sharing
Screen sharing is exactly what it sounds like. You'll be sharing the screen of a Mac and as such any thing you do on that screen will be visible to both the local and remote user. You can initiate a connection via finder from under the shared sidebar or via a VNC client such as TightVNC.
To enable Screen Sharing do the following.
- Start System Preferences.
- Select Sharing.
- Check Screen Sharing to on.
Apple Remote Desktop
Apple Remote Desktop is the bigger more capable brother to Screen Sharing. Of the plethora of things ARD can do such as manage multiple computers, take inventory, and deploy software, it too has a remote screen sharing capability. It's a bit of overkill for simple screen sharing and data access but you can get more information from Apple directly if you think you're the type to take advantage of all of the features. Like Screen Sharing, you'll need to roll your own out of network connection method, like VPN or the like, and you can use both the Finder and a VNC client to make a remote screen connection. Here's how to setup Apple Remote Desktop on your Mac.
- Start System Preferences.
- Select Sharing.
- Check Remote Management to on.
Third party solutions
If you're not the type to want to configure VPNs or firewalls to enable internet screen and file sharing access, you'll be happy to know that there do exist third party programs you can purchase that allow for Back to My Mac capabilities.
Screens 4
Edovia Screens 4 allows for Desktop access (For around $30) with an optional remote internet access service called Screens Connect that takes care of all of the dirty connectivity work for you. It's easy to setup and syncs across all of your iCloud devices with both macOS and iOS versions. It is completely compatible with VNC server/client software.
LogMeIn
LogMeIn offers a robust Remote Desktop solution that isn't VNC compatible but has its own proprietary Remote Desktop client software that takes care of all of the connectivity issues. Although costly at around $350/year, it's used by professional individuals and businesses alike and offers excellent support services for those times that access to your Mac's Remote Desktop is critical.
Final comments
I'm the type of person that likes to roll my own Remote Desktop solutions by using FOSS wherever possible. I'm lucky enough to have a static IP at my home so connectivity is not an issue when I am traveling. I use it nearly every time I travel. Will losing Back to My Mac be an issue for you? Will you roll out your own solution or will you have to pay for a third party for remote connections to your desktop and files? Do you have other suggestions for Remote Desktop access? Let us know your thoughts in the comments!
Related resources
We test and review VPN services in the context of legal recreational uses. For example:
1. Accessing a service from another country (subject to the terms and conditions of that service).
2. Protecting your online security and strengthening your online privacy when abroad.
We do not support or condone the illegal or malicious use of VPN services. Consuming pirated content that is paid-for is neither endorsed nor approved by Future Publishing.
We may earn a commission for purchases using our links. Learn more.
U.S. and Afghan forces successfully captured insurgents using an iPhone app
When their specialist kit failed, soldiers turned to an iPhone to get the job done.
...">Deploy A Quick Vpn Alternative For Mac(26.02.2020)